VPN technology and configurations have evolved over the years, offering innovative features designed to address the modern challenges and problems that the average internet user faces today. For those interested in exploring a variety of secure, fast, and reliable VPN options, the article Top VPN Services: Secure, Fast, and Reliable Choices provides an excellent overview of the best VPN providers currently available.
Double VPN, while not a new idea, has recently become more popular after some well-known VPN providers began offering this configuration as a built-in feature in their clients.
But what is Double VPN, what are the different types of this form of VPN connection, and most importantly, what benefits can you expect from a Double VPN configuration?
These are typical questions from VPN users who have heard of the term “Double VPN” but do not know the details of its underlying mechanisms.
This article is an attempt to educate users on what the fancy-sounding Double VPN is.
What does Double VPN do?
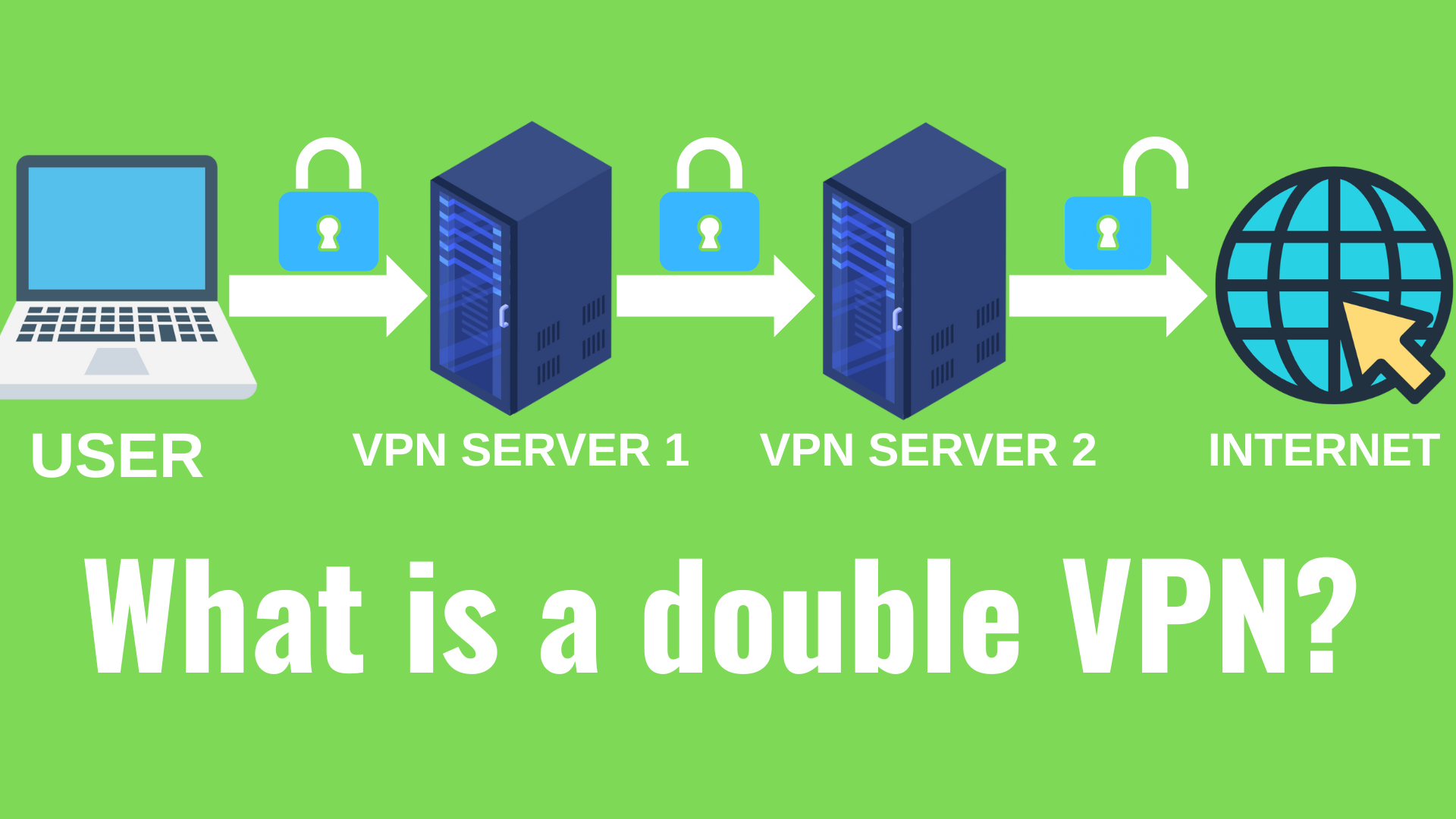
The concept of a double VPN is extremely simple: instead of your internet traffic going through one VPN server, a double VPN connection routes your traffic through two VPN servers, encrypting your data twice.
The journey of your internet traffic in a double VPN setup looks like this: data from the user’s device is encrypted and sent to the first VPN server. That server encrypts your data again and forwards it to the second VPN server (which itself may or may not encrypt it again, depending on the length of your VPN chain). The second server finally decrypts your data and then forwards it to the destination server (the website you want to visit) securely.
Because there are two servers involved, your IP address changes twice and your online fingerprint is spread across two separate, remotely located servers instead of just one, in addition to repeating the encryption process twice. This configuration greatly increases your security, but the additional encryption comes at the cost of speed.
That covers the basic concept of a double VPN.
Types of Dual VPN/Multi-Hop Configuration
Essentially, Double VPN is a form of VPN chaining, also known as VPN cascading or multi-hop networking. In a Double VPN configuration, the chain consists of two VPN servers. But this concept can be extended to form a VPN chain, which consists of multiple VPN connections that are networked together.
In these “multiple” configurations, your VPN traffic can travel through three, four, or even more separate VPNs before reaching its final destination.
There are two commonly used multi-hop modes: cascading and nested chains.
Cascade VPN connection
A cascade VPN connection type typically refers to a setup that uses two or more VPN servers from a single primary VPN service. In this setup, your traffic passes through several different servers from the same provider before reaching its final destination. With each server or “hop,” you are assigned a new IP address.
Generally, the more servers you route your traffic to, the more times your IP address will be shuffled. Note that in a cascade connection, there are multiple servers, but only one VPN service or provider.
Nested chain connection
A nested chain connection uses more than one VPN service to form a connection. That is, it uses services from two or more separate providers and then configures them so that one VPN works on top of the others.
A nested chain configuration is more complex to set up than others and requires some technical know-how to set up successfully. As such, it is not as common as cascaded systems.
Difference between Onion over VPN and DoubleVPN/Multihop
It’s not just VPN servers that can be cascaded together to form a more secret layer of internet connection. Another common method of accessing the internet with relatively more privacy and anonymity is through the Tor browser.
Tor is short for The Onion Router, and it’s basically a decentralized network of nodes that repeatedly encrypt your traffic, dispersing your trail and increasing your security through a series of encryptions.
Tor is generally more popular with bloggers and journalists who are intimidated by the government for reporting any story or issue that might be critical or offensive to the authorities.
You can combine the power of Tor and VPN together to increase your web security and privacy to a higher level than either of the two technologies could provide if used separately. This is VPN chaining, and some providers like NordVPN refer to Tor as Onion over VPN.
Onion over VPN is different from double VPN and multi-hop connection. In Onion over VPN, user data is transmitted through a VPN network and an onion network, two separate technologies. However, a double VPN or multi-hop configuration is a configuration that consists entirely of VPN servers without any onion nodes involved.
This is the key difference between these two types of network chains.
Setting up a double VPN
There are several options for configuring a double VPN, covering a range of levels of complexity.
1 Use a VPN with a built-in Double VPN feature
The simplest way is to use a VPN service that comes with a double VPN feature as part of its package. Enabling this feature will allow you to connect to one server as an entry node and a second server as an exit node.
For example, with double VPN enabled, your provider will allow you to connect through a chain of servers consisting of a Netherlands-Switzerland connection. This means that your traffic will first arrive at a server in the Netherlands and then be routed to the destination server via Switzerland, receiving two different IP addresses at each stage of the connection.
2 VPN + Router Connection
If you don’t have a VPN with a built-in double VPN feature, you can use a VPN + router combination to set up a double VPN connection.
This method involves setting up a VPN on your router and then on your device. In this setup, your traffic will always follow a VPN chain that starts from your router and ends with the second VPN client that you set up on your device.
But this can only work if you know how to set up a VPN on a router.
3 Virtual Machine
This is one of the more technically challenging methods of setting up a dual VPN. Basically, it involves using software like VirtualBox or Hyper-V to install a virtual operating system on your current operating system.
Once you have two operating systems installed this way, you can turn on your VPN client from the primary operating system, and then connect the second VPN client from your virtual operating system.
You should see that the IP address you get on the virtual machine matches the IP address of the VPN server you are connected to from the original operating system.
Keep in mind that you must have a powerful computer with a powerful processor and a lot of RAM to run the virtual operating system stably. The installation of the virtual machine itself has a significant impact on computers.
Multiple VPN encryption, decryption, and tunneling processes between two operating systems will further burden your system.
So you should only use this method if you are confident in your system’s ability to handle a virtual machine.
4 Browser Add-on + VPN Client
Many VPN providers offer browser extensions along with their desktop clients. You can use browser extensions to form a VPN chain consisting of a client and an add-on.
This is not exactly a true double VPN connection because browser extensions only encrypt your browsing sessions, leaving other programs and applications as they are.
What’s more, the browser extensions offered by most providers are proxies, so you’ll end up with a VPN-proxy chain, rather than a VPN-over-VPN connection.
However, this is still one of the easiest ways to add an extra layer of security to your online browsing sessions.
5 Nested Chains with Different Providers
All of the above dual VPN configuration methods can be done either using different servers of a single VPN provider or using multiple VPN providers with their own separate networks chained together using any of the methods described above.
However, this method will be more expensive than using a single VPN provider as you will have to incur the cost of separate subscriptions for each provider you use.
Benefits of Double VPN
When it comes to the privacy and security of your online traffic and identity, double VPN offers the following specific benefits:
- IP protection: Because a double VPN connection assigns two IP addresses at each of the two VPN routing stages, your real IP address is hidden even more effectively than regular VPN encryption. The first server in a double VPN chain will assign you an IP address that is completely different from the one assigned by the second server. As a result, anyone trying to track you online will lose track of you due to the multiple IP address changes as your data moves across the linked network.
- Security from exposure: If one of the VPN providers’ servers is seized by authorities, they will still not be able to easily track you because your traffic is rerouted through two servers. This is not a problem if the VPN does not store any sensitive logs at all, but dispersing your presence across multiple nodes provides better privacy.
- Protocol mixing: You can alternate between two different protocols to increase online security. For example, you can use the UDP protocol to connect to the first server and TCP to connect to the second server.
Some bloggers point out that a major benefit of double VPN is that it adds another layer of encryption. This is not entirely true. For example, if an ISP uses AES-256 for encryption, it will still remain AES-256 no matter how many servers you connect to at once.
Also, there is no real benefit to double-encrypting your traffic, given that protocols like AES-256 are extremely secure and do not require additional cryptography to effectively fend off attacks and interceptions by hackers.
So the main benefit of double VPN is that it changes your IP address multiple times and allows you to use mixed protocols. These actions help enhance privacy and anonymity, but double-encrypting your data is just a gimmick that has no real value, nor is it something most ISPs actually do when routing your traffic through multiple hops.
Disadvantages of Double VPN
Double VPN has several performance-related drawbacks that may make it undesirable for many VPN users:
- Slow Speeds: Sending your data through multiple VPN servers and protocol layers will inevitably increase the load on your network system. Your data will have to travel a longer distance to reach the same destination, resulting in slower pings and connection speeds. So, if you don’t want to compromise on speed, it’s best to avoid using a double VPN.
- High Processing Power: Double VPN configurations are resource-intensive and can impact the performance of your entire computer or device. This isn’t a problem if your VPN offers built-in multi-hop functionality, but it can seriously impact performance if you’re using a virtual machine to set up a double VPN.
Should you use double VPN?
Double VPN does have a number of benefits, but it is a resource-intensive connection method that can significantly reduce internet speeds. Therefore, for most users, it is not necessary. However, there are situations where such protection is entirely justified.
Journalists
If you work in journalism, especially in countries with limited freedom of speech, a double VPN can be an additional layer of security. It will help to better protect both your identity and your sources of information.
Activists and protesters
In countries where public events may be subject to surveillance, increased privacy is especially important. Using a double VPN can reduce risks in cases where it is important to maintain anonymity and protect personal data.
To protect personal privacy
Privacy is a natural right for everyone. No one should be allowed to monitor your online activity or access personal data unnecessarily. If you attach great importance to your privacy, a double VPN can help increase your level of anonymity on the Internet and make it more difficult for those who would like to track you.
VPN that offer Double VPN
NordVPN is one of the few VPNs that offers a Double VPN feature built into the client. The Double VPN feature is available for multiple platforms, including Windows, Android, and MacOS.
NordVPN also offers Onion over VPN, which combines the Tor network with a traditional VPN configuration for users who want the benefits of both types of topologies. Overall, NordVPN is a great choice due to its powerful combination of speed, server network, Double VPN, and a host of additional features.
Double VPN Alternative from ProtonVPN Secure Core Technology
In addition to the classic Double VPN feature, ProtonVPN has its own Multi-Hop counterpart — Secure Core technology. It also builds a chain of VPN servers, but does it in a special way: first, your traffic passes through secure servers in countries with strict privacy laws, such as Switzerland, Iceland, or Sweden. And only then does the connection exit through regular servers in other countries. You can read more about this in our ProtonVPN review.
This two-step route provides additional protection against sophisticated attacks and hacking of the final VPN server. Even if someone manages to gain access to the exit server, it will not be possible to associate your data with your real IP address.
All Secure Core servers are owned by ProtonVPN and are located in data centers with a high level of physical security, and their disks are fully encrypted. This eliminates the risk of encryption keys being stolen even with physical access to the equipment.
Secure Core is a great choice for those who want to not only hide their IP address, but also protect themselves as much as possible from possible surveillance by government agencies, providers, or other third parties. This is another reliable way to organize multi-level VPN protection for those who want to always stay one step ahead.
Conclusion
Double VPN offers important benefits for users with high privacy requirements. Although there are only a few providers with built-in double VPN functionality, it is possible to set it up yourself using the methods described above.
Do you think Double VPN is worth using for privacy protection, or is it overkill? I would love to hear your thoughts in the comments section below.






