
A proxy server is a program that mediates between the device from which you access the Internet and the sites you visit. If you use a proxy, when you visit different sites the information will first go through the proxy server and only then it will come to you or the sites.
Using certain types of proxy servers you can change your IP to the IP of a proxy server, mobile operator or another user. So, for example, if you are in Australia and you need Polish IP, you just need to buy a Polish proxy. The figure shows schematically the processes of direct data exchange and data exchange using a proxy server between two computers in the network.
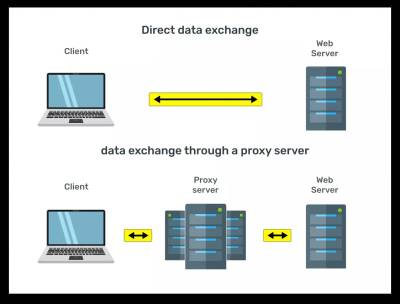
Modern anti-detect browsers support major proxies (including IPv6), including Socks5/Http/Https/SSH.
Why proxies are needed
Many people try to use proxies for fraudulent activities such as sending SPAM, I do not recommend doing so, there are other ways to do it. And any proxy provider will most likely just block your account.
Proxies are used to:
- Access blocked sites. You can use proxies to hide your real IP and replace it with the one given by the proxy server. For example, to bypass the blocking of Instagram, LinkedIn (and other social networks), work in the Etsy store, parsing with Key Collector or ZennoPoster.
- Masquerade as a real user. For example, to arbitrage traffic or publish reviews. It is important to note that just changing the IP is not enough to mask the data. This is due to the fact that in addition to the IP address, websites also look at many other parameters: data about your device, screen settings, time zone, language, etc. That’s why you should additionally use an anti-detect browser to stay anonymous online, protect your data or mimic real users.
- Accelerate access to sites. Some proxies add sites to the cache so that they load faster when re-opened.
- Protect your data online. Using some types of proxies, all sites you visit will see the IP address of the proxy server, not yours. This will prevent sites from collecting information about you, for example, to show ads. Moreover, some proxies can be used to protect against IP hacking since the attackers will not see your real address. However, proxies alone are not enough to fully protect your data.
- No limit on the number of connections. Some sites and services restrict the number of connections or requests at a time from a single IP address. Using a proxy can help remedy this situation.
- Check access to the site from all over the world. Using a proxy, you can connect to a site to check its availability from different countries or ISPs and networks.
Proxy like a VPN? The difference for the user is that the VPN uses end-to-end encryption, the data transmitted is protected from the point of entry to the point of exit. A proxy server is a less secure technology and cannot be used without an anti-detect browser.
What are proxies
Proxies are divided into different types depending on the level of anonymity, location, supported protocol, etc. Let’s look at proxies in a cross-section of the two most popular ones.
Anonymous proxy
Anonymous proxies replace your IP address with their address, and the proxy server address is displayed in the HTTP line. With such a proxy, the visited site will not know your real IP, and sites will see that you are using a proxy. You will be much less trustworthy because of this.
Anonymous proxies are not very good for parsing and working with Facebook, Google and other complicated sites. They can, however, be used to visit sites that are blocked in a particular country.
Elite anonymous proxies do not tell anyone that you are using a proxy and do not specify your or your IP. The advantage of these proxies is that the resource you are visiting cannot see that you are using a proxy. Such proxies are good if you want to imitate real user data, for traffic arbitrage, posting reviews, etc.
Transparent proxies – proxies that do not mask your IP address. They are used, for example, to speed up your access to the website: they add sites to the cache and, therefore, when you open the website again, it will load already saved data. Such proxies are often used by companies to save traffic.
Proxy placement
- Server proxies. They are also called data-center proxies. They are proxies in which you get the IP of a data center. Such proxies are inexpensive, but they have some disadvantages:
- They are defined as proxies. Because of this you will not be able to imitate the behavior of a normal user. On the other hand, some sites may deny you access to their resources because you are hiding your identity.
- They are not unique. Such proxies can be used by several users at once.
- They are defined as proxies. Because of this you will not be able to imitate the behavior of a normal user. On the other hand, some sites may deny you access to their resources because you are hiding your identity.
- They are not unique. Such proxies can be used by several users at once.
These proxies are good for visiting blocked sites, but are unlikely to pass anti-fraud systems.
- Resident proxies are IP addresses issued by ISPs to their private users. Such proxies can be used by only one person at a time and are not identified as proxies. Resident proxies do not raise any suspicions and are therefore used to bypass antifraud systems. Resident proxies have two major drawbacks: they cost considerably more than server proxies and are often slower.
- Mobile proxies are proxies issued by a mobile operator. Such proxies are dynamic and the service provider may assign an IP address to thousands of subscribers at a time. Being aware of this peculiarity, antifraud systems do not block such IPs and look for other ways to identify a user to see if it is a real person. Similar to resident proxies, mobile proxies cost more than server proxies because they help bypass antifraud systems.
Proxy protocol
- HTTP proxy. As the name implies, this type of proxy only supports and is suitable for browsing web pages and downloading files from web services running on Standard 80. HTTP proxies are not suitable for viewing sites that work only through the SSL protocol. HTTP proxies cannot be chained together.
- HTTPS (CONNECT) proxy or HTTPS proxy. Proxies of this type support the HTTP CONNECT method, which involves HTTP tunneling. In this process, the top-level protocol (HTTP) is used to transmit a lower-level protocol (TCP). These proxies can connect to any port. Thus, proxies of this type can work with virtually any network application (TCP), including web servers over a secure SSL protocol. HTTP tunneling provides anonymity to HTTPS proxies and allows them to work in a chain.
- SOCKS proxy. Almost any network application can work through a SOCKS proxy. For example, you can use a SOCKS proxy to work with your mail client (POP3, SMTP, IMAP). Another distinguishing feature of SOCKS proxies is that you can use several SOCKS proxies in a chain simultaneously, increasing your level of anonymity. SOCKS proxies are always anonymous because they operate on a low-level protocol and do not update the HTTP headers. There are three versions of the protocol: SOCKS4, SOCKS4a and SOCKS5. The most functional is SOCKS5. It allows you to make DNS queries on the proxy side using the UDP protocol and the BIND method, opening the port for incoming connections.
How to choose a proxy
Proxies should be chosen based on the tasks you need to solve. For example, it is better to use resident proxies or mobile proxies for traffic arbitrage, work with electronic wallets and cryptocurrencies. But regular server proxies are enough for bypassing blocked sites in a particular territory.
From the point of view of a proxy server user, the fewer people have access to a given proxy, the better. First, the fewer users use a particular proxy, the higher its speed. Second, a breach of any online service’s rules by one user will result in a ban, making the proxy unusable for all other users of that service. Thus, proxies of all types can be conditionally divided by limited access to them.
How much does a proxy cost
There are many services online that offer free proxies. Such proxies are definitely not suitable for working with Google or Facebook, since these IP addresses are already blocked. Moreover, they can be dangerous for your device.
We recommend that you choose proxies from companies that specialize in selling proxies and have been on the market for several years. It will help to avoid unscrupulous sellers who may deceive you, hurt you or your device.
The cheapest proxies are server proxies. Mobile and resident proxies are more expensive.
Proxy providers
Below is a list of the best trusted proxy providers.
AstroProxy – free trial version
AstroProxy provides dynamic proxies of three types. The external IP can be changed unlimitedly within the selected address pool.
Resident and mobile proxies are based on real devices in dozens of countries. This increases resistance to bans and captcha thanks to NAT technology. Proxies are distributed by country, city, and provider.
Advanced and simple settings panel in a single window. Top up your account with fiat and cryptocurrency, traffic packages are available (from 100 MB) at a low price.
AstroProxy promises unlimited access to all proxies when renting a port. All IP addresses work using HTTPS and SOCKS protocols of your choice.
- Trust evaluation (Trustpilot): 4.4
- IP Number : 1,000,000+
- Geographic coverage : 20+ countries
Use the free trial with no limits on time, type, number, and geolocation of proxies.
Asocks resident and mobile proxies at one price – $3/GB
Resident and mobile proxies at one price – $3/GB. More than 150 GEO, with the ability to target up to the city by ASN. You can pay for the service with any card or cryptocurrency.
Asocks – premium proxy service for any business tasks. You need to pay only for the spent traffic at a super price of $3=1GB. The most stable proxies on the market, successfully connect to any software and programmes.
Avoid blocking and bypass any restrictions with antidetect browser and proxies from Asocks.
Proxys – inexpensive individual and private proxies
- Price ProxysIo from 1.47 USD 30 days/each
- Proxy types: Private, general
- Trust Score (Trustpilot): 4.4
- IP number: 10,000+
- Geographical coverage: 12 countries
- Free trial : no
- Promotion Code : no
Proxys is a proxy rental service with over 10,000 IP addresses from 12 countries. The provider’s main product is IPv4 and IPv6 proxies. All of them can connect using HTTP and SOCKS protocols. The service also provides 24-hour support and refunds within 24 hours after purchase. All proxies are like programs for anonymous browsing and no logs are kept.
Conclusion
There are many proxy providers on the market and each one provides different types of proxies. Not everyone needs expensive private proxies, sometimes public proxies are enough. So, when choosing a proxy type and a proxy provider, it is up to you what you want to do.






Hi there! This article couldn’t be written any better! Reading through this post reminds me of my previous roommate!
He continually kept talking about this. I will send this
post to him. Fairly certain he will have a great read.
I appreciate you for sharing!
Hey very nice website!! Man .. Excellent .. Superb .. I will bookmark your website and take the feeds additionally?
I’m satisfied to search out so many useful info right here within the put up, we need work out more techniques on this regard,
thanks for sharing. . . . . .